Kerberos is built in to all major operating systems including. Kerberos and LDAP are commonly joined together including in Active Directory to provide a centralized user directory LDAP and authentication Kerberos services.

Kerberos Art From Soul Sacrifice Art Artwork Gaming Videogames Gamer Gameart Conceptart Illustrati Fantasy Creatures Creature Concept Mythical Monsters
Er lässt sich zur sicheren Authentifizierung in TCPIP-Netzwerken einsetzen und stellt Usern Tickets zur Nutzung von Services zur Verfügung.

Kerberos. Information in this section provides theoretical background on the use of the Kerberos protocol in an authentication process. Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services. Kerberos arbeitet mit symmetrischer Verschlüsselung und verlangt die Autorisierung durch eine vertrauenswürdige dritte Partei um die Identität von Benutzern zu verifizieren.
Kerberos is adopted by a huge number of industries so any new weaknesses in its security protocol or in underlying modules are quickly corrected. ευρωπαϊκής πλατφόρμας Forest Fire Information System FFIS καθόσον ότι. Kerberos Authentication Explained.
It serves as. You could use Kerberos a network authentication protocol developed by MIT in order to verify your identity without exposing login information. Den Ausgang der Unterwelt bewacht.
LDAP the Lightweight Directory Access Protocol stores information about users groups and other objects like computers in a central location. After initial domain sign on through Winlogon Kerberos. In Kerberos Authentication server and database is used for client authentication.
While it is derived from symmetric key algorithms which use the same key for encryption as. στρέμματα μόνο σε Αττική και Εύβοια σε σύγκριση με. Kerberos allows companies to use its centralized authentication server for using protocols that help build security walls for software applications.
The core product backbone of the entire Kerberosio ecosystem completely free and open source. Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. Der Begriff Kerberos steht sowohl für ein Protokoll als auch dessen Implementierung und ermöglicht eine sichere Authentifizierung in einer unsicheren Umgebung.
Deploy your own video surveillance system in a few minutes anywhere you want using Raspberry Pi Docker or Balena Cloud. According to myth Kerberos you might know him as Cerberus guards the Gates to the Underworld. Der Name bezieht sich auf den Höllenhund der in der griechischen Mythologie den Ein- bzw.
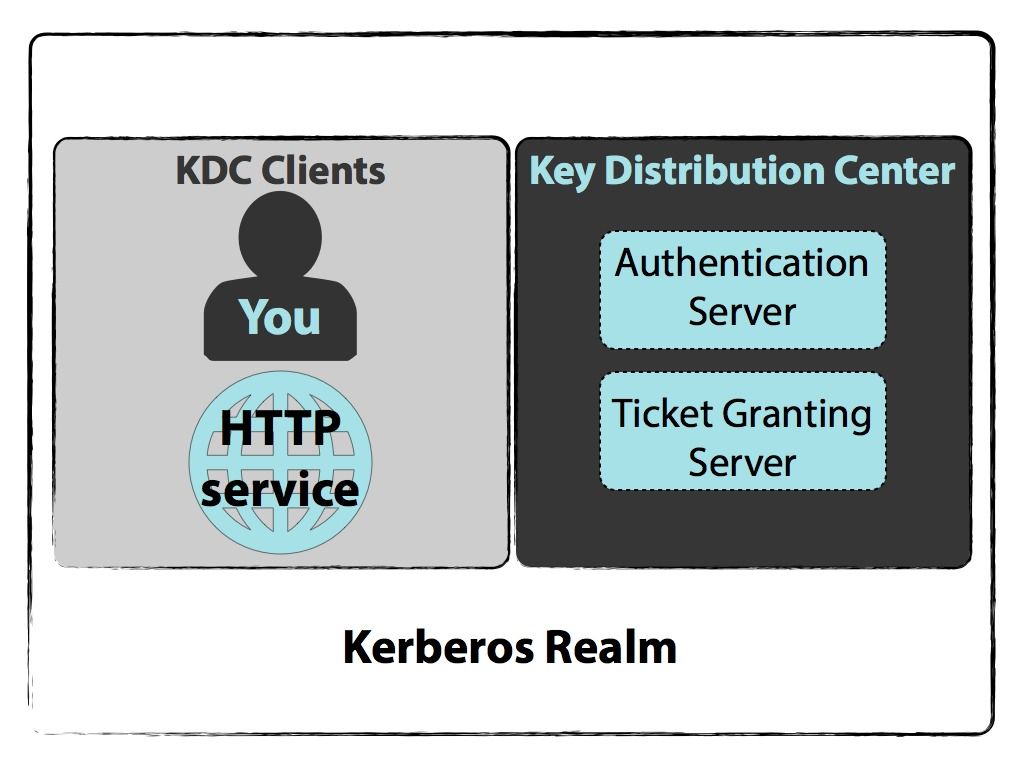
The weaknesses of Kerberos are. The Kerberos authentication. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC.
Passwörter müssen nicht mehr über das Netzwerk übertragen werden. Kerberos can only be adopted by Kerberos aware applications. Scope of Using Kerberos.
In the modern world MIT Computer Scientists used the name and visual of Kerberos for their computer network authentication protocol. Kerberos is a protocol for authenticating service requests between trusted hosts across an untrusted network such as the internet. Hes a big 3 headed dog with a snake for a tail and a really bad temper.
Das Protokoll basiert auf dem Needham-Schroeder-Protokoll. This is background information that can add to a developers understanding of what is happening behind the scenes in an SSPI process that uses the Kerberos Version 5 protocol. The Kerberos protocol uses strong cryptography so that a client can prove its identity to a server and vice versa across an insecure network connection.
Kerberos ist ein verteilter mit Tickets arbeitender Authentifizierungsdienst. Named after the guard dog of Hades Kerberos uses mutual authentication requiring both the user and server to prove their identities. If a non-authorized user has access to the Key Distribution Center the whole authentication system is compromised.
Kerberos was created by MIT as a solution to these network security problems. Kerberos tickets represent the clients network credentials. Transparent video surveillance for everybody everywhere.
It can also provide for simple authentication however these native protocols. However practically the implementation of the Kerberos authentication process is much more complex. The Kerberos authentication process employs a conventional shared secret cryptography that prevents packets traveling across the network from being read or altered as well as protecting messages from eavesdropping and replay or playback attacks.
Weil Kerberos drei Entitäten für die Authentifizierung verlangt und Computer sehr erfolgreich sicher gehalten hat. After a client and server has used Kerberos to prove their identity they can also encrypt all of their communications to assure privacy and data integrity as they. In this blog we discussed what Kerberos is and the authentication workflow of Kerberos in a simple way.
How does Kerberos work. It could be a problem to rewrite the. Each user and service on the network is a principal.
Now that we have learned what is Kerberos let us next understand what is Kerberos used for. Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials. οι πυρκαγιές βρίσκονται ακόμη σε εξέλιξη έγιναν στάχτη πάνω από 270000.
The main components of Kerberos are. Microsoft setzt Kerberos als Standardauthentifizierungsmethode in Windows-basierten Netzwerken ein.

Kerberos Architecture Computer Help Windows Server Microsoft

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

Cerberus Or Kerberos In Greek And Roman Mythology Is A Multi Headed Usually Three Headed Dog Or Hel Greek And Roman Mythology Greek Mythology Greek Myths

Kerberos Gp1 Jpg Image Cops Group Pictures Jin Roh

Cluster Dedicated Kdc Kdc On Master Node Emr Big Data Master
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

Freeletics Workout Kerberos Das Workout Geht Uber 3 Runden Mit Jeweils 3 Ubungen Pro Runde Freeletics Freeletics Ubungen Freeletics Workout

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux

Kerberos Architecture Computer Help Windows Server Microsoft

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Kerberos Explained Security Companies Band Patches Microsoft

Authentication Fails When A Windows Client Accesses A Cifs Share Because The Kerberos Authentication Ticket Is Cached In 2021 Windows Client Fails Clients

Cracking Kerberos Tgs Tickets Using Kerberoast Exploiting Kerberos To Compromise The Active Directory Domain Active Directory Innovation Technology Domain

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base

What Is Kerberos And How It Works Social Media Infographic Computer Network Infographic

Kerberos Saga Jager Enemy Character Design

Selecthiveql Nifi Connection Hives
YOU MAY LIKE :


